DIN 66399 FOR DATA AND DOCUMENT DESTRUCTION
When reading about security in data and document destruction, you will keep coming across the same term: DIN 66399.
You may wonder: What does this DIN standard mean and why is it so important?
Until September 2012, DIN 32757 was the applicable standard for the destruction of data media. However, it was highly ambiguous and its wording was not clear enough. This meant there were various ways of implementing the standard. In order to establish uniformity, the existing standard was revised and finally replaced by DIN 66399.
DOCUMENT DESTRUCTION AND DATA MEDIA DESTRUCTION IN BERLIN
- Good value
- Sustainable
- Self-delivery
- Comfortable
- Periodically


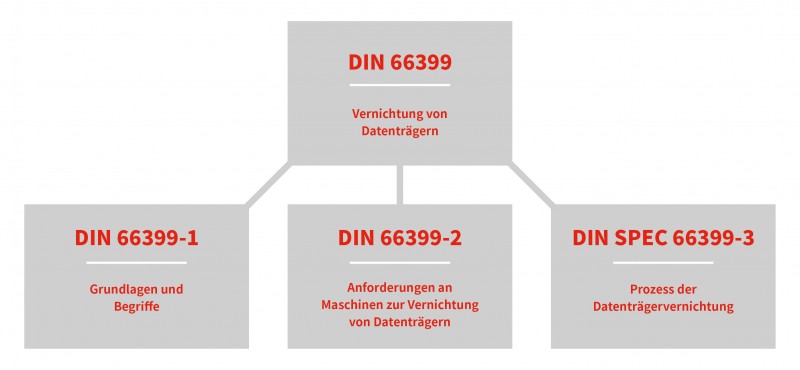
What is DIN 66399?
DIN 66399 consists of three parts. The first two parts are already recognised standards. The first part defines the terms and principles; while part two focuses on the requirements for machines for data and document destruction.
Part three of DIN 66399 (SPEC) is considered a “pre-standard”, which means that its status as an official standard is still pending. This part of DIN 66399 defines the processes involved in the destruction of data media. This results in clearly worded technical and organisational measures.
Various groups contributed to the definition and classification of the new standard: machine manufacturers, the German Federal Office for Information Security and various document destruction service providers were involved in the process.
What do protection requirements and protection class mean in the context of document destruction?
For the purposes of document destruction, data is divided into different protection classes to take into account the economic efficiency and the need for protection. The protection requirement depends on how much protection the data needs. Personal data, for example, needs a higher level of protection than advertising brochures.
The degree to which the data requires protection determines the choice of protection class and security level. This classification results in different technical and organisational measures that have to be fulfilled for document destruction.
Protection requirements, protection classes, security levels and the precise organisational measures are always determined by the “data controller”. The data controller is the owner of the data.
The different protection classes
Protection class 1 - normal sensitivity for internal data
This protection class applies to information that was intended for larger groups of people from the outset. If this type of data were to be compromised, the negative impact on the company would be limited. In the event of data protection violations, the affected party could only be slightly affected in their social position and economic circumstances.
Protection class 2 - high sensitivity for confidential data
Applies to information that is only intended for a smaller group of people from the outset. Data protection violations would have serious consequences for the company and could violate contractual obligations or laws. The affected party could therefore be significantly affected in their social position and economic circumstances.
Protection class 3 - very high sensitivity for particularly confidential and secret data
Protection class 3 pertains to information that was intended from the outset for a very small group of persons specified by name. Any data protection violations would have existence-threatening consequences or would violate professional secrets, laws and contracts.
The security levels at a glance
- Security level 1: General data – recovery with simple effort
- Security level 2: Internal data – recovery with special effort
- Security level 3: Sensitive and confidential data – recovery with considerable effort
- Security level 4: Particularly sensitive and confidential data – recovery with exceptional effort
- Security level 5: Data that must be kept secret – recovery with indefinable effort
- Security level 6: Secret high-security data – recovery currently not technically possible
- Security level 7: Top secret data – recovery impossible
Combination of protection classes and security levels
The table below shows the combinations of protection classes and security levels recommended by the DIN committee. The table clearly shows that the combination of a very low protection class with a very high security level and vice versa does not make sense from the committee’s point of view. The data owner (so-called “data controller”) is always responsible for the correct classification.
The assignment of protection classes and security levels
The following table enables you to assign the three protection classes and security levels. However, each case should be individually decided by means of a risk analysis. When dealing with data of different protection classes, it may be more economical to separate it according to the security levels and protection classes. However, if the data is mixed, the data media must be destroyed according to the highest protection class and security level.
|
Assignment of protection |
S1 | S2 | S3 | S4 | S5 | S6 | S7 |
| protection class 1 | x | x | x | ||||
| protection class 2 | x | x | x | ||||
| protection class 3 | x | x | x | x | x |
Increasing the security levels
The destruction of documents in large facilities and the mixing and blending of large volumes of different data offers a further significant increase in security. In such cases, DIN 66399 allows for a higher security level while maintaining the same particle size.
However, the security level can only be raised by one step and up to a maximum of security level 4 if information is displayed in its original size. Since we destroy large quantities of material in our modern shredding facility, we meet this criterion.
Data media destruction process according to DIN 66399 SPEC
Part 3 of DIN 66399 (DIN 66399-3) is still merely a "pre-standard" (SPEC). This means that it is not yet a fully-fledged DIN standard. Despite this, it is already treated as a binding standard in the commercial environment.
The destruction of data media is understood as a complete process in which the individual process stages are to be examined, safeguarded and implemented. The data owner, i.e. the data controller, therefore remains formally responsible until data destruction has been completed. Once the agreed security level has been reached, the data is considered to have been deleted.
The entire process is usually divided up between the data controllers and external service providers. It is particularly important in this context to consider the segregation of duties and to define the technical and organisational measures.
3 possible process variants exist here:
Variant 1: Data media destruction by the data controllers themselves
Variant 2: Data media destruction by a service provider on site
Variant 3: Data media destruction by an external service provider
Determination of the risk structure
After determining a process variant, it is necessary to check in advance whether the technical and organisational requirements of the corresponding protection class and security level are satisfied. When defining the protection class and security level, the data controller should answer the following questions:
- Which information is to be classified in which protection classes?
- Which security level should apply?
- Which of the 3 variants should and can be selected?
- Which technical and organisational measures should be defined for the overall process?
Certification according to DIN 66399
The DIN standard very precisely defines what conditions a company must fulfil in order to guarantee the corresponding protection classes and security levels. The relevant certification bodies make it possible to certify the company and confirm compliance with the various provisions.
Of course we hold such a certificate.
Here you can find this and further certificates: Haberling certificates


Your contact
HABERLING TEAM
Document- and data carrier destruction
in cooperation with

